Security Best Practices
UpdatedFrom our side, we’re working hard to keep your data safe, but there are also a few measures you, as an Account Admin, can take to make your Customer.io account security bulletproof.
1. Do not share login credentials
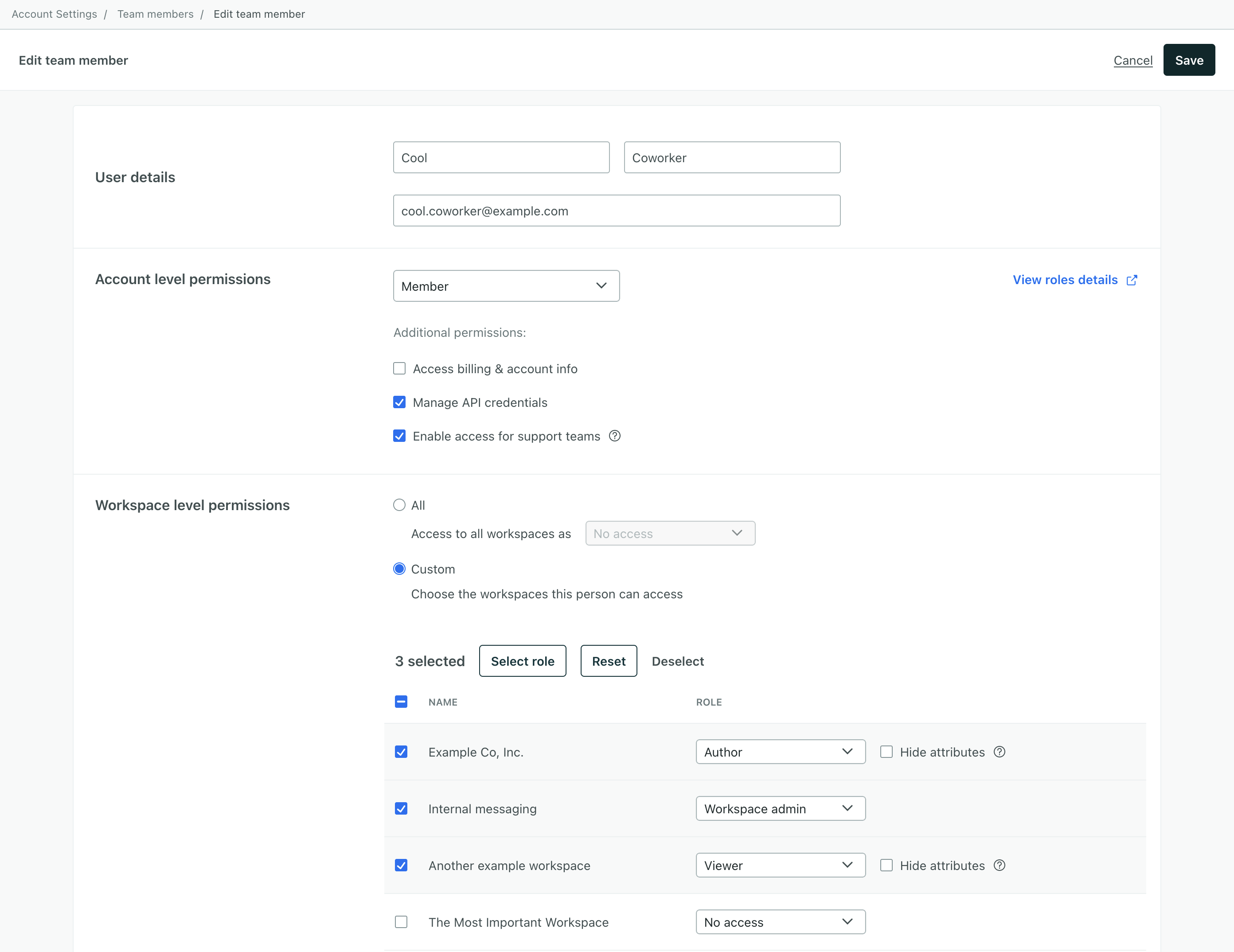
Add named accounts for all of the people in your team who will be collaborating on your messaging content and strategy. Customer.io allows you to add as many team members as you need - with different levels of access.
2. Limit your team to the access level they need
When you add team members, you can set their permissions at the account and workspace levels. If you manage a large team, you’ll likely want to limit the access levels that people have to ensure that they can only see and edit what they need to.
At the Account level, you probably want to limit the number of Admin-level team members. Account Admins have full access to your account and all your workspaces. You can limit access by setting your teammates account roles to Member. Then you can determine which workspaces each member has access to, and the level of access they have within each workspace.

3. Ensure your login id is a valid email address
If your Customer.io account still uses an old email address you no longer have access to, update it as soon as possible. You run the risk of being locked out of your account in case of an attack, and you’re also missing out on important notifications sent by our team.
4. Use a secure password
It’s crucial to use a strong password that cannot be easily guessed or cracked by malevolent individuals trying to retrieve your customer database. While remembering long, complicated passwords might be difficult to do on your own, a password manager can make this process painless.
5. Enable Single Sign-on (SSO)
If you use a common single sign-on provider like Google Suite, Okta, or Microsoft Entra ID, you can enable SSO to manage access to your Customer.io account. This adds an extra layer of protection to team members logging in to the account and removes the risk of managing extra passwords.
We also support SSO with SAML 2.0 for Cloudflare, Jumpcloud, and Okta. If you use one of these providers, you can enable SAML to manage access to your Customer.io account.
6. Notify other Account Admins ASAP if you’ve lost access to your account
If you lost your 2FA device and are worried someone else might use it to gain access to your company’s Customer.io account, ask another Account Admin to remove your user and re-add it. The initial 2FA authentication method will become invalid and you can add a new one.
If you’re the only Account Admin, our technical support team can verify your identity and reset your access.
7. Review your team’s exports regularly
This will allow you to detect any suspicious activity early on and take action against the offender. If you need additional information regarding the downloads performed by a particular team member like the IP address and which exports they retrieved, reach out to our support team and we’ll be happy to help.

8. Remove team members who leave your company or change roles
It’s best practice to audit access to your account to keep your account secure. Have you removed team members that are no longer with your company? Did someone change departments and no longer needs access?
To remove access, go to Team Members, click , and then select Delete next to that person’s email address.

If you’re an account admin, you can export team members to help you audit access to your workspaces. Click Export to CSV at the top of Team Members.
You can also periodically review the Last Login date on the Team Members page to determine if your teammates still need access to your account.
9. Keep your contact information up to date
Periodically check your legal and technical email address on a regular basis so we can notify you about potential issues with your account. You’ll find your contact information under Account Settings > Account.
10. What to do about compromised credentials
Following the best practices in this document should help prevent (and minimize the impact of) unauthorized access to your account.
But, if you suspect your API credentials have been compromised or an unauthorized individual has gained access to your account, you should:
- Remove the malicious actor. This may be a former team member or someone whose access to your account should have lapsed!
- Rotate your API credentials. This ensures that the bad actor can’t affect your data.

